A Comprehensive Certification Program for Foreign Businesses in Europe
The European Union’s Artificial Intelligence Act (EU AI Act), effective August 1, 2024, represents a significant regulatory shift for businesses using artificial intelligence (AI) within the EU. This landmark legislation introduces stringent compliance requirements, impacting how companies develop, deploy, and govern AI systems. For businesses operating in or entering the European market, understanding and adapting to these regulations is not just a necessity—it is a competitive imperative.
The **Certified Expert on the EU AI Act Program**, led by Steinbeis Augsburg Business School, offers a specialized training solution tailored for professionals. This program provides in-depth knowledge of the EU AI Act, practical tools for compliance, and strategies to ensure AI is implemented ethically and responsibly, with full simultaneous Chinese translation for seamless participation.
Six Key Challenges and Opportunities Under the EU AI Act
**1. Financial Impacts on BRICS+ Businesses
Adhering to the EU AI Act introduces significant costs for companies coming from BRICS countries. For instance, Hong Kong-based AI startup Dayta AI projects cost increases of 20% to 40%, primarily due to stricter data quality and representativeness requirements. These added costs necessitate careful selection of training data and a re-evaluation of existing AI workflows.
**2. Competitiveness in the European Market**
While compliance ensures access to the lucrative EU market, the regulatory burden poses competitiveness challenges. Unlike the relatively unregulated AI markets in the US and China, the EU’s stringent rules require significant adaptation. However, companies that achieve compliance can gain trust and a competitive edge in the European landscape.
**3. Specific Requirements for AI Systems**
The EU AI Act categorizes AI systems into three risk tiers:
– **Prohibited Systems**: Includes AI used for social scoring, banned for its ethical and privacy concerns.
– **High-Risk Systems**: Subject to rigorous requirements, including risk management, transparency, and compliance certification.
– **Low-Risk Systems**: These require minimal oversight but must meet basic transparency guidelines.
Understanding these categories is critical for businesses to align their operations with EU standards.
**4. Compliance Timelines and Transition Periods**
The phased rollout of the EU AI Act gives businesses time to adapt, with key milestones such as:
– **February 2, 2025**: Prohibition of certain AI practices and enforcement of general provisions.
– **May 2, 2025**: Introduction of Codes of Practice to assist early adopters.
Full compliance is expected by 2030, requiring companies to prepare now for a smooth transition.
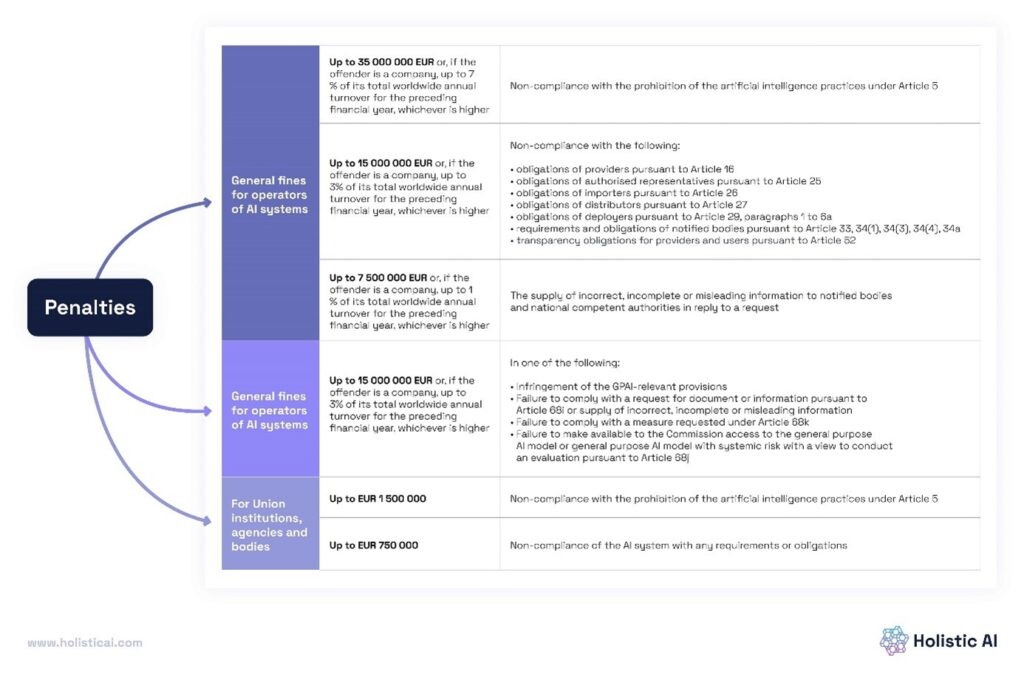
**5. Risks of Non-Compliance**
Penalties for non-compliance are severe, including fines of up to €30 million or 6% of global annual revenue, whichever is greater. These strict penalties underscore the need for rigorous adherence to the regulations.
**6. Steps for Ensuring Compliance**
BRICS+ businesses can prepare for the EU AI Act by:
– **Conducting Risk Assessments**: Classify AI systems based on risk tiers.
– **Enhancing Transparency**: Ensure systems are explainable to users.
– **Improving Data Quality**: Meet EU standards for training data.
– **Maintaining Documentation**: Keep detailed records of AI development and deployment.
Why This Program is Essential for AI Professionals
The **Certified Expert on the EU AI Act Program** addresses these challenges by offering a comprehensive curriculum designed to equip participants with the expertise to navigate the complexities of the regulation.
Program Benefits
- Master the legal framework and requirements of the EU AI Act.
- Learn to implement AI responsibly, ensuring ethical and societal considerations are met.
- Develop strategies to align AI systems with European compliance standards.
- Gain practical tools to conduct risk assessments, enhance transparency, and manage data security.
Program Content
1. AI in Everyday Business
Understand how to integrate AI effectively to improve efficiency, enhance quality, and streamline decision-making processes.
2. The EU AI Act
Gain a thorough understanding of the Act’s legal provisions, including its risk-based approach and compliance obligations.
3. Risk Analysis and Data Protection
Learn to identify and evaluate risks associated with AI systems, while ensuring compliance with data protection standards.
4. Ethical AI Implementation
Explore strategies for embedding ethical principles into AI development and deployment, addressing societal and moral impacts.
5. Compliance and Certification
Prepare for the EU AI Act certification by implementing governance structures and maintaining proper documentation.
Four Program Highlights
1. **Tailored for Chinese Businesses**
Specifically designed for Chinese companies operating in or expanding to Europe, addressing unique challenges and opportunities.
2. **Multilingual Accessibility**
Delivered with simultaneous Chinese translation, ensuring participants were fully engaged with the content.
3. **Expert-Led Training**
Gain insights from leading European AI and legal experts, blending academic rigor with practical applications.
4. **Global Networking Opportunities**
Connect with like-minded professionals across industries and regions, fostering collaborative growth.
Who Should Attend?
- Chinese business leaders navigating AI compliance in Europe.
- Legal and compliance professionals ensuring organizational alignment with the EU AI Act.
- AI developers and technology specialists seeking to enhance their understanding of regulatory frameworks.
Your Path to Compliance and Success
With the EU AI Act transforming how AI is governed, businesses must act decisively to align with these new standards. By joining the **Certified Expert on the EU AI Act Program**, you’ll position yourself and your organization as leaders in ethical, responsible, and compliant AI usage.
Program Overview
Module 1 (Suzhou, China): AI in Everyday Business
Understand how to integrate AI effectively to improve efficiency, enhance quality, and streamline decision-making processes.
Module 2 (Suzhou, China): The EU AI Act
Gain a thorough understanding of the Act’s legal provisions, including its risk-based approach and compliance obligations.
Module 3 (Suzhou, China): Risk Analysis and Data Protection
Learn to identify and evaluate risks associated with AI systems, while ensuring compliance with data protection standards.
Module 4 (Hamburg, Germany): Ethical AI Implementation
Explore strategies for embedding ethical principles into AI development and deployment, addressing societal and moral impacts.
Module 5 (Hamburg, Germany): Compliance and Certification
Prepare for the EU AI Act certification by implementing governance structures and maintaining proper documentation.
Examination (Hamburg, Germany): Final exam of modules 1 to 5 and presentation of certificates (ceremony) with press.
Each module includes case studies, interactive workshops, and opportunities for peer learning, ensuring you gain both theoretical and practical insights.
Program Overview
- Purpose of the Program
This certification develops AI Act experts capable of driving sustainable strategies, measuring performance, and ensuring compliance with key regulations. - Learning Format
The program is structured around five intensive modules, combining online live sessions and on-site workshops in Suzhou, China (three modules), and Hamburg, Germany (three modules). This enables participants to gain a global and localized perspective on AI Act practices. - Expert Instruction with Global Accessibility
All sessions are led by industry-leading European experts and practitioners, with simultaneous English and Chinese translation to ensure seamless engagement and understanding.
Who should attend:
- CEOs, CFOs, COOs, and other C-level executives who want to sell their products to Europe. Either by shipping directly to the European customer or by selling the products to suppliers.
The key is to:
a. Provide the relevant evidence in the AI Act on time.
b. Avoid the horrendous contractual penalties caused by errors in the documentation.
Benefits:
- Obtain and sustain orders
- Establish a professional network at the same level with potential customers and suppliers in Europe and the BRICS countries.
(2) Executives or management consultants, who want to professionally prepare their entry or transition into an AI management role.
Benefits:
- Be faster to market and receive appropriate project requests and assignments.
- Avoid trial and error and costly loss of time.
- Gain security by creating a concrete “plan” together with industry experts; also integrating it into a network.
(3) People already working as interim managers, who want to “fine-tune” their business model and market development considering current market changes.
Benefits:
- More suitable project requests
- Better utilization at the right daily rate
- More fun at work – Integration of expert tips into one’s own work
- Integration into a network
The mix of participants from all countries is a very “stimulating” mix for everyone.
Program Goals and Outcomes: What You Will Achieve
1. Expertise in AI ACT Standards and Practices:
- Deep understanding of AI ACT.
- Knowledge of cutting-edge methods to measure and manage AI ACT performance.
- Ability to prepare sustainability reports aligned with global standards.
- Awareness of the latest developments in AI ACT regulations and reporting frameworks.
2. Practical Skills for Immediate Application:
- Crafting sustainable corporate strategies and integrating AI goals.
- Identifying and managing AI risks and leveraging opportunities for innovation.
- Communicating AI initiatives effectively to internal and external stakeholders.
- Advising companies on meeting AI ACT requirements.
3. Leadership and Influencers:
- Position yourself as a sought-after AI ACT consultant in an increasingly sustainability-driven global economy.
- Build a network of like-minded professionals and industry leaders.
- Concrete steps to implement this personal business plan
- Your business model and personal business plan
- Your career plan with concrete steps
- Clarity about “My core competencies and what I like to do”
- Network with practical tips from experienced industry insiders
- Reflection with practical tips from experienced industry insiders
- Network for further support along the way (individual peer-to-peer mentoring and access to the Master of Excellence network)
- Master of Excellence in AI ACT certificate from a renowned global think tank
- Individual follow-up coaching by the speakers and mentors (dates to be agreed upon individually)
What Sets This Program Apart
- Focus on Businesses in Europe for BRICS+ countries
Tailored for Chinese companies expanding into Europe, this program addresses the unique challenges and opportunities faced by professionals, including regulatory compliance and sustainable growth strategies. - Global Learning with Local Context
Gain exposure to European AI ACT leadership while understanding its relevance to the Chinese business environment. - Cutting-Edge Content
Dive into AI ACT topics such as carbon reduction, energy efficiency, sustainable supply chains, and innovative governance models. - Networking Opportunities
Build a robust network of Chinese and European business leaders, creating opportunities for collaboration and growth.
A Basic Conviction that Guides You Through the Course
Leaders are successful:
- … when they do what they enjoy and find “meaningful”
- … when they do what they are “really good at” – and better than their “competition”
- … when they offer their customers added value with what they do
- … when they are “entrepreneurs” for themselves
- … when you can market and monetize your offering, i.e. the market rewards your service at an appropriate price.
All five conditions should be met for sustainable success.
Procedure
Before the course
- Check if it makes sense to participate and register. Upon request: Non-binding preliminary discussion (video call) with Andreas Renner from Steinbeis Business School Hamburg Germany, Dr. Lucas Bretz from GAMI Suzhou China in English or German
- Binding registration of participants HERE
- Preparation of participants for the face-to-face part. Participants will receive a preparation assignment in advance (time commitment 1/2 day).
Workshops in the presence
- Duration three days in Suzhou, China (content see above)
- Duration three days in Hamburg, Germany (content see above)
In the days following the face-to-face part
- Individual development of a business model/business plan integrated into your life concept or your own company.
- Documents and instructions will be presented and explained in the classroom.
Examination
- Online presentation of the business model/business plan by the participants plus feedback/discussion (60 minutes per participant). Online on 2 different dates of your choice.
- Certification upon completion of requirements.
After passing the exam: Coaching, mentoring and networking
- Coaching of the practical implementation of the participants by the workshop leaders (one meeting per participant with an instructor).
- Mentoring by interim manager peers (by mutual agreement)
- Inclusion in the LinkedIn group (Certified AI ACT Consultants network)
Dates and Schedule
Modules 1 & 2 & 3: Suzhou, China – September 4-5, 2025
Modules 4 & 5: Hamburg, Germany – September 18-19, 2025
Exam: Hamburg, Germany – September 20, 2025
Start in the morning at 9 am. End at 17:00.
Program Outcomes
Upon completion, you will:
- Earn a recognized certification as a Certified AI ACT Consultant, a distinction that sets you apart in the global market.
- Be equipped to assist companies in overcoming ESG challenges, ensuring compliance, and driving sustainability initiatives.
- Possess a unique blend of global insights and local expertise, making you a valuable asset to any organization.
Certification, Certificate, and Seal
Examination: Preparation and presentation of a business plan based on anindividual career plan: Written through submission to instructors and successful online presentation with questions answered and discussion.
Lecturer certificate: The certificate is awarded by the Future Academy of the global think tank Diplomatic Council (UN reg.) together with UNITEDINTERIM.
Seal: Each participant will receive a “Master of Excellence in AI ACT” seal, jointly awarded by GTEC and Steinbeis Business School. The seal is perfect for self-promotion (website, email signature, social media…).
Take the First Step Toward Sustainability Leadership
Join the Certified AI ACT Consultant Program and empower your business to thrive in a sustainability-driven world. Whether you are a leader aiming to elevate your organization’s AI performance or an entrepreneur seeking a competitive edge, this program is your gateway to success.
Visit our website at steinbeis-ifem.de for more information and registration.Together, let’s build a sustainable future.